Here is how to join a server running Ubuntu Linux to Active Directory Domain and also permit just some users or groups to log into this server.
First, ensure that your Linux VM uses the AD as the primary DNS server.
# Install the required packages
sudo apt-get install -y krb5-user samba sssd sssd-tools libnss-sss libpam-sss ntp ntpdate realmd adcli
# Set your timezone if necessary
timedatectl set-timezone America/Cuiaba
# Try the realm discover to check if the Domain is reachable
# The domain name must be entered in UPPERCASE
realm discover CONTOSO.LOCAL
Initialize Kerberos using the kinit command.
kinit -V administrator@CONTOSO.LOCAL
# Add the computer to the domain using the same account as before
realm join --verbose CONTOSO.LOCAL -U 'administrator@CONTOSO.LOCAL' --install=/
# Prevent all users from log into this server
realm deny -a
# Permit a specific group to log into this server
realm permit -g LinuxAdmins@contoso.local
# Configure automatic home directory creation
echo "session required pam_mkhomedir.so skel=/etc/skel/ umask=0077" >> /etc/pam.d/common-session
# Add the permited group to the sudoers file
echo "linuxadmins@contoso.local ALL=(ALL) NOPASSWD:ALL" >> /etc/sudoersThat’s it, first I will try to connect to the server using the default Administrator account without being a member of the permitted group.

The connection failed, now let’s put the Administrator into the group.
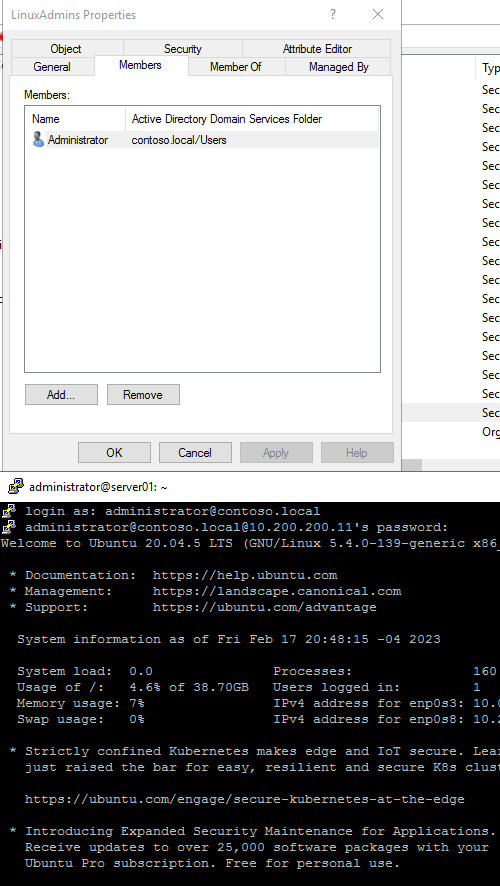
Was able to connect and also elevate with sudo